Table of contents
- Amazon EC2 with Lab:
- Introduction:
- EC2 sizing & configuration options:
- EC2 User Data:
- EC2 Instance Types - Overview:
- EC2 Instance Types – General Purpose:
- EC2 Instance Types – Compute Optimized:
- EC2 Instance Types – Memory Optimized:
- EC2 Instance Types – Storage Optimized
- EC2 Instance Types: example:
- Introduction to Security Groups:
- Security Groups Deeper Dive:
- Security Groups Diagram:
- Security Groups Good to know:
- Referencing other security groups Diagram:
- Classic Ports to Know:
- Create an EC2 instance using the AWS Management Console:
- Thank you, and happy Learning!
Amazon EC2 with Lab:
Introduction:
Amazon EC2 (Elastic Compute Cloud) is a web service provided by Amazon Web Services (AWS) that offers resizable compute capacity in the cloud. Here are the key points about Amazon EC2:
Virtual Servers: EC2 allows you to launch virtual servers called instances. These instances can be customized based on your requirements, such as the choice of operating system, instance type, storage options, and networking configurations.
Scalability: EC2 provides scalable compute capacity, allowing you to easily scale up or down based on your needs. You can increase or decrease the number of instances, adjust computing resources like CPU and RAM, and handle sudden traffic spikes efficiently.
Instance Types: EC2 offers a wide range of instance types optimized for different use cases. Each instance type has varying combinations of CPU, memory, storage, and networking capacity, catering to specific workload requirements.
Pricing Options: EC2 offers various pricing options, including On-Demand Instances (pay-as-you-go), Reserved Instances (pre-purchased capacity), and Spot Instances (bid-based pricing). This flexibility enables you to optimize costs based on your workload characteristics and budget.
Storage Options: EC2 provides multiple storage options, such as Amazon Elastic Block Store (EBS) for persistent block-level storage, Amazon S3 for object storage, and instance store volumes for temporary storage.
Networking and Security: EC2 instances can be placed in Virtual Private Cloud (VPC) environments, allowing you to have complete control over your network settings. You can configure security groups, and network access control lists (ACLs), and apply various security measures to protect your instances.
Integration with Other AWS Services: EC2 seamlessly integrates with other AWS services, enabling you to build highly scalable and resilient architectures. You can leverage services like Amazon RDS for managed databases, Amazon S3 for storage, and Elastic Load Balancing for distributing traffic to instances.
Management and Automation: EC2 provides tools for managing and automating your instances, such as AWS Management Console, AWS Command Line Interface (CLI), and APIs. These tools allow you to monitor your instances, automate deployments, and efficiently manage resources.
Overall, Amazon EC2 is a powerful service that allows you to run virtual servers in the cloud, providing flexibility, scalability, and control over your computing resources.
EC2 sizing & configuration options:
Operating System (OS): Choose between Linux, Windows, or Mac OS for your EC2 instances, based on your application's compatibility and requirements.
Compute power & cores (CPU): EC2 instances offer various instance types with different virtual CPU (vCPU) counts, allowing you to select the appropriate compute power for your workload.
Random-access memory (RAM): EC2 instances provide different RAM capacities, ranging from gigabytes to terabytes, enabling you to choose the right amount of memory to support your application's performance.
Storage space:
1. Network-attached (EBS & EFS): Utilize Amazon Elastic Block Store (EBS) for durable block-level storage and Amazon Elastic File System (EFS) for scalable and shared file storage.
2. hardware (EC2 Instance Store): Leverage the high-performance, ephemeral storage directly attached to the EC2 instance.
Network card: EC2 instances come with network cards of varying speeds, determining the network performance, while a Public IP address enables direct internet connectivity for the instance.
Firewall rules: Control inbound and outbound traffic using security groups, specifying protocols, ports, and IP ranges to ensure secure access to EC2 instances.
Bootstrap script (EC2 User Data): Configure your instance at launch with a bootstrap script using EC2 User Data, automating actions such as software installation and custom configurations for streamlined and consistent deployments.
EC2 User Data:
EC2 User Data allows us to bootstrap instances by executing scripts during startup. Bootstrapping involves running commands when a machine starts, and the User Data script runs only once during the initial instance launch. It enables automating tasks like installing updates, software, and downloading files. The script has root user privileges, granting necessary permissions for executing desired actions and configurations during instance initialization. It provides flexibility to customize and automate various setup tasks to streamline deployments and ensure consistent configurations across instances.
EC2 Instance Types - Overview:
You can use different types of EC2 instances that are optimized for different use cases. https://aws.amazon.com/ec2/instance-types
AWS follows a consistent naming convention for its EC2 instances, such as "m5.2xlarge". The naming convention provides key information about the instance:
"m" indicates the instance class, representing a balance between compute, memory, and networking resources.
"5" denotes the generation of the instance type, with newer generations often offering improved performance and features.
"2xlarge" represents the size within the instance class, indicating the specific configuration and capacity of the instance.
EC2 Instance Types – General Purpose:
Ideal for diverse workloads like web servers or code repositories.
Provides a balanced combination of computing power, memory, and networking capabilities.
The t2.micro instance, which we will be using in the course, falls under the General Purpose EC2 instance category.

EC2 Instance Types – Compute Optimized:
Designed for compute-intensive tasks demanding high-performance processors.
Ideal for batch processing, media transcoding, high-performance web servers, HPC, scientific modeling, machine learning, and dedicated gaming servers.

EC2 Instance Types – Memory Optimized:
Offers fast performance for workloads that require processing large datasets in memory.
Well-suited for high-performance relational/non-relational databases, distributed web scale cache stores, in-memory databases optimized for BI, and real-time processing of big unstructured data.

EC2 Instance Types – Storage Optimized
Designed for storage-intensive tasks with high, sequential read and write access to large datasets on local storage.
Well-suited for use cases like high-frequency online transaction processing (OLTP) systems, relational and NoSQL databases, cache for in-memory databases (e.g., Redis), data warehousing applications, and distributed file systems.

EC2 Instance Types: example:
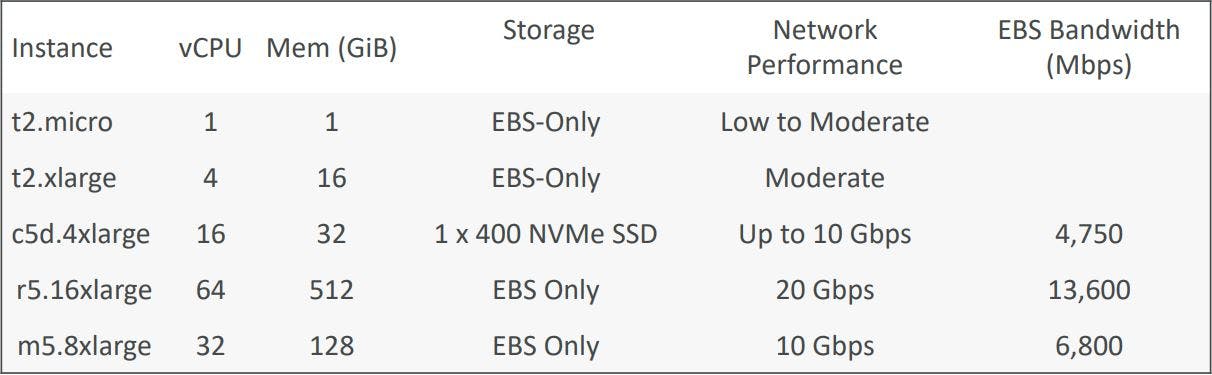
Great website: click here
Introduction to Security Groups:
Security Groups are a foundational component of network security in AWS.
They regulate inbound and outbound traffic for EC2 instances, controlling access to and from the instances.

Security groups consist of allow rules, specifying which traffic is permitted.
Rules within security groups can reference IP addresses or other security groups, providing flexibility in defining access controls.
Security Groups Deeper Dive:
Security groups are acting as a “firewall” on EC2 instances
They regulate:
• Access to Ports: Security groups allow you to specify which ports on an EC2 instance are open and accessible to incoming traffic. You can define rules to permit or deny access to specific ports based on your requirements. For example, you may choose to allow incoming HTTP traffic on port 80 or SSH traffic on port 22.
• Authorized IP Ranges (IPv4 and IPv6): You can configure security group rules to restrict access based on the source IP address or IP range. This provides a way to control which IP addresses are allowed to communicate with your EC2 instances. You can define both IPv4 and IPv6 addresses/ranges in security group rules.
• Inbound Network Control: Security groups enable you to manage inbound network traffic that is directed toward your EC2 instances. By defining rules, you can allow incoming connections based on the protocol (such as TCP, UDP, ICMP), port numbers, and source IP addresses or IP ranges. These rules determine which incoming network traffic is permitted to reach your instances.
• Outbound Network Control: Similarly, security groups also allow you to control outbound network traffic originating from your EC2 instances. You can specify rules to authorize or block outgoing connections based on the protocol, port numbers, and destination IP addresses or IP ranges. These rules dictate which outbound traffic is allowed to leave your instances.

Security Groups Diagram:

Security Groups Good to know:
Attachable to Multiple Instances: You can associate a security group with multiple EC2 instances, allowing you to apply the same set of rules to those instances.
Region/VPC Combination: Security groups are specific to a region and a virtual private cloud (VPC). They cannot be applied to instances in different regions or VPCs.
Security Group's Location: Although security groups are associated with EC2 instances, they function at the network interface level. If traffic is blocked by a security group, the EC2 instance won't receive or perceive that traffic.
Separate Security Group for SSH Access: It is recommended to maintain a separate security group specifically for SSH access to enhance security. This allows you to control SSH traffic separately from other types of traffic.
Timeout Issues: If your application is not accessible and times out, it could be due to a misconfiguration or restriction in the security group rules.
"Connection Refused" Errors: If your application returns a "connection refused" error, it typically indicates that the application itself is not running or not launched correctly, rather than a security group issue.
Default Inbound and Outbound Traffic: By default, all inbound traffic is blocked, which means you need to explicitly define the rules to allow incoming connections. On the other hand, all outbound traffic is authorized by default, meaning instances can communicate with external resources unless explicitly blocked.
Referencing other security groups Diagram:

Classic Ports to Know:
Port 22: Used for SSH (Secure Shell) to log into a Linux instance securely.
Port 21: Used for FTP (File Transfer Protocol) to upload files into a file share.
Port 22: Used for SFTP (Secure File Transfer Protocol) to upload files using SSH.
Port 80: Used for HTTP to access unsecured websites.
Port 443: Used for HTTPS to access secured websites.
Port 3389: Used for RDP (Remote Desktop Protocol) to log into a Windows instance remotely.
Create an EC2 instance using the AWS Management Console:
Sign in to the AWS Management Console.
Open the EC2 Dashboard.

Click on the "Launch Instance" button.

Choose an Amazon Machine Image (AMI) that suits your requirements. This includes selecting the operating system and pre-installed software.

Select an instance type that matches your needs in terms of compute power, memory, and storage.

Choose an existing key pair or create a new one for SSH access.

Configure the instance details such as the network settings, subnet, and security group.

(Optional) Add storage volumes to the instance.

Scroll down to the "Advanced Details" section.

In the "User data" field, enter the script or commands you want to run on the instance at launch. This can be used for automated configuration and setup.
#!/bin/bash # Update the instance sudo yum update -y # Install necessary packages sudo yum install -y httpd # Start and enable the httpd service sudo systemctl start httpd sudo systemctl enable httpd # Set up a custom index.html file echo "<h1>Hello World from $(hostname -f) in AZ</h1>" > var/www/html/index.htmlConfigure the number of instances, and Review the summary.

Click on Launch the instance.

Monitor the instance startup process and wait for it to be running.

Copy the instance Public IP and paste it into the browser.

You will get the result of your user data script:

